
What is a Cybersecurity Framework?

 A cybersecurity framework serves as a roadmap to organize cybersecurity risk management activities for an organization.
A cybersecurity framework serves as a roadmap to organize cybersecurity risk management activities for an organization.
Frameworks are comprised of industry guidelines, best practices and standards, and can be voluntary or mandatory. As an example, the U.S. Department of Commerce’s National Institute of Standards and Technology’s NIST Cybersecurity Framework is a voluntary framework that can be adopted if an organization so chooses. But others are required, like one framework that’s mandatory for any organization globally that accepts, processes, stores, or transmits credit card information.
Implementation of a formal framework may benefit your organization in terms of helping to improve your security posture and enhance your resilience against cyberattacks or other compromises. Frameworks generally define a number of core functions that can help your organization assess your cyber programs current state, improve cyber defenses, enhance incident detection capabilities, and minimize impact and improve recovery from a cyber event, should one occur. Frameworks may also provide metrics and other tools to help measure progress in regards to framework adoption and assessment of security posture.
Note that frameworks are not maturity models and are not meant to assess the level of maturity that your organization has in regards to cybersecurity. Frameworks provide overarching guidance and can be used as a blueprint on how to manage cybersecurity risk.
Cyberattacks and compromises may be launched by an external adversary or may originate from employees, contractors, or anyone with trusted physical and/or virtual access to IT and other technology-based assets, such as a disgruntled employee intentionally destroying or stealing data.
Significant events such as nation state activity targeting healthcare organizations are changing the way organizations perceive and assess cyber risk. Traditionally, confidentiality of information has been the focus of healthcare organizations, but now, given the changing threat landscape, healthcare organizations are not only concerned about confidentiality, but also the integrity and availability of information as well.
Watch Brian Selfridge, partner at IT Risk Management for Meditology, talk with HIMSS TV about mapping frameworks together to find the best fit for your organization.
Does My Organization Need a Cybersecurity Framework?
According to the HIMSS Cybersecurity Survey, there has been no universal adoption of any particular framework. Further, not all healthcare organizations have adopted any kind of framework to manage risk.
While the healthcare sector has made some progress in terms of transitioning from a compliance-based security mindset to a risk-based one, additional improvement needs to be made. Far too many organizations still approach cybersecurity from a compliance perspective with major concerns being data breaches and HIPAA compliance. Yet, HIPAA does not provide guidance on how organizations should go about putting together a cybersecurity program in order to achieve robust security and resiliency to deal with today’s sophisticated and targeted threat actors.
In other words, being compliant with a checklist approach, vis-à-vis HIPAA, does not necessarily mean that an organization will be secure. Cybersecurity frameworks, on the other hand, provide the tools to build out cybersecurity programs, stand up policies and procedures, and implement necessary technical controls to safeguard the confidentiality, availability and integrity of information.
RELATED: The Case for a Cybersecurity Framework
In addition to helping with internal matters, a framework can also help your organization manage risks with external partners such as business associates, other healthcare providers, software manufacturers, and IT service providers. In this vein, frameworks provide both a common language and methodology for helping to manage cybersecurity risk.
Additionally, adopting appropriate frameworks can help organize cybersecurity risk management activities. Without having such a structure in place, it may be difficult for your organization to manage cybersecurity risk.
A struggle many organizations face is that other organizations they interface with—whether healthcare providers, vendors, or others—may have a weak security posture. The weak security posture may be due to a variety of factors, such as a lack of cybersecurity framework adoption and implementation. Far too many organizations shift the responsibility to vendors to protect their assets and information. Yet, significant risk may remain, as not everything can be outsourced. Your organization needs to take ownership and responsibility for its own security postures.
How Do You Measure Success?
During implementation as well as steady state, your organization should measure how well your security systems perform relative to your chosen framework.
Your organization’s cybersecurity mission, goals and objectives should align with its larger mission, goals and objectives. Therefore, any framework should be able to translate the security requirements from the highest strategic level of governance via specific security programs to the technical execution, i.e., the implementation of the actual security processes and controls. Consequently, when measuring the progress and quality of your security program, you need to measure it on all levels and assure that controls, programs and governance do what they are expected to do.
This concept is illustrated below. As a simple example, you may achieve 100% compliance of your security controls, but if the wrong controls to meet program or governance objectives were picked, you still have a failing security program.
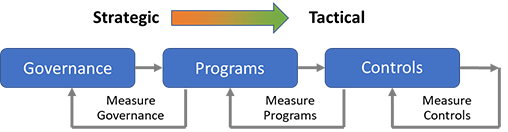
Conceptual illustration of security governance, programs and controls | Source: Axel Wirth
Also, your organization needs to differentiate between the implementation phase of your framework and the final steady state. During implementation, we would not expect to meet all desired requirements, therefore, would need an implementation plan that provides a moving target to measure the progress of your framework implementation over time. Such measurement would be able to detect deviation from the plan but also should be able to detect defects in the plan itself, as certain security requirements may have been overlooked.
Realistically, we need to accept that in the context of a security program, steady state is a relative term. Security is never static, changes in the threat landscape, IT infrastructure, or business objectives all lead to the need to continually assess and adopt your security program.
It is also important to understand that any framework selected should be applied judicially. Not every organization (or part of an organization) needs the same level of security. Not complying with all aspects of a framework is a perfectly valid decision and organization may make—but it has to be a conscious decision based on a full understanding of the respective risks. At the same time, some organizations or parts may find they need additional requirements beyond what is provided by the chosen framework. Cybersecurity frameworks are certainly not “one size fits all.”
There are several layers to a mature cybersecurity model. Consequently, your organization will need to apply different methods and measures. On the business level, the main concern is about the cost of security and the risk to the business. On a program level, the focus is on processes and compliance, whereas on the technical (security controls) level, performance and reliability are key.
Measuring Success of Governance
Review programs to ensure they meet governance objectives:
- Audits
- Comparison against industry performance
- Security cost and impact analysis
Measuring Success of Programs
Review controls against program requirements:
- Audits
- Comparison against industry benchmarks
- Comparison against framework
Measuring Success of Controls
Review requires a somewhat different approach as controls are basically measured against themselves, i.e., how well do they perform? To that end, controls are typically measured by using established tools, benchmarks and security metrics:
- Assess compliance of security architecture, e.g., through comparison against established best practices
- Measure compliance of IT assets, e.g., through tools like standards and vulnerability scanners or pen testing
- Assess compliance of information assets, e.g., through tools like data loss prevention
- Assess compliance of workforce through questionnaires, exercises and security metrics, e.g., measure the click rate in response to an email phishing exercise
- Establish regular reporting of key security metrics, e.g., basic measures like number of incidents or more complex but valuable metrics like mean time to identify, contain, and respond
- Incident analysis and post mortem
Overall, regular assessment and quantification of security metrics should provide your organization with sufficient information to rate security maturity as well as detect and correct deviations.
No organization is immune to a cyberattack or other compromise. Any organization, regardless of industry, location, or size are possible targets. Today, healthcare organizations are coming to the realization that they are as much at risk as any other industry.
A framework is necessary to obtain a holistic perspective of what your organization needs to do, what its baseline is, and where it needs to go in terms of managing its cybersecurity risk.
Cybersecurity and Security Incidents in Healthcare Infographic
Healthcare organizations face a barrage of significant security incidents in addition to the challenges faced during the COVID-19 pandemic. Get key insights into what the landscape looks like in this infographic.



